PRODUCTS
Secure Logic Infrastructure
A comprehensive cybersecurity framework designed to protect digital and physical assets in industrial environments.

How SLI Works:
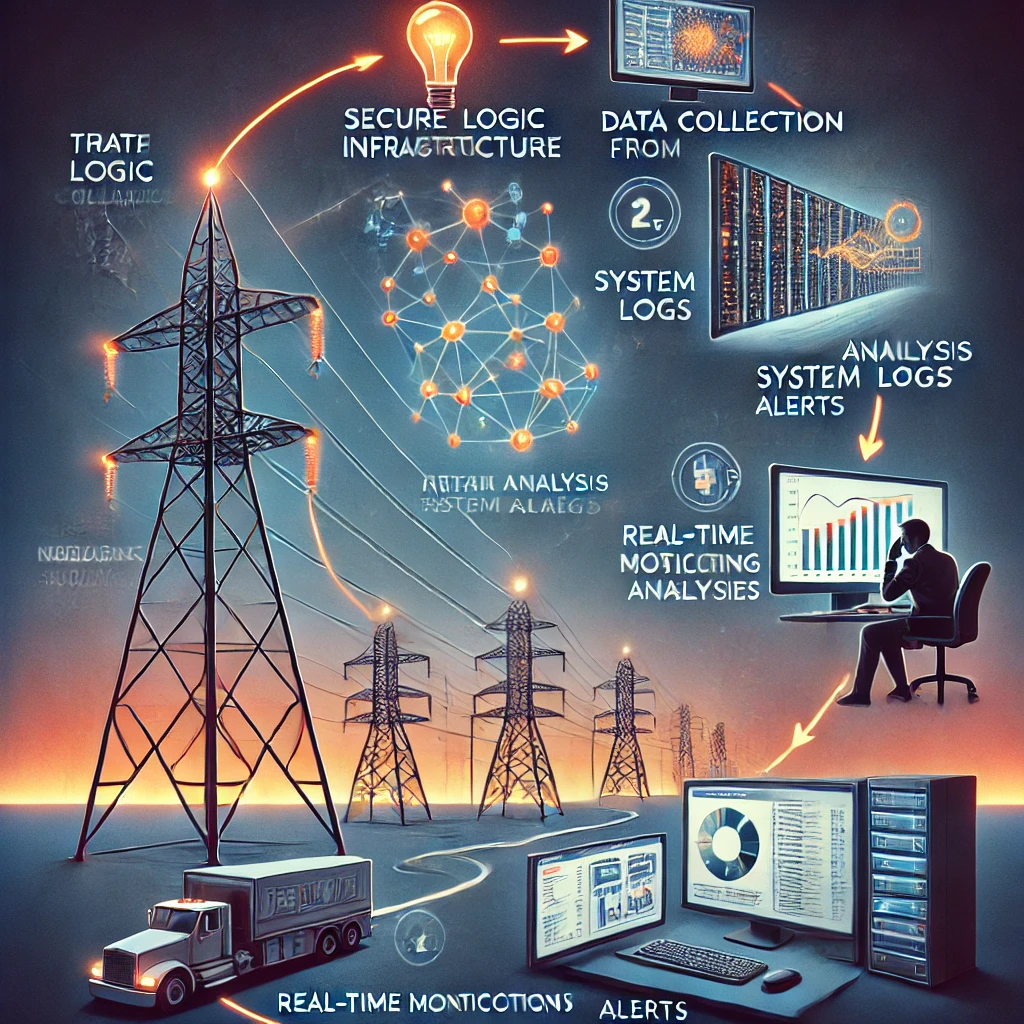
- Mobile Group's Secure Logic Infrastructure (SLI) provides a comprehensive cybersecurity framework designed to protect digital and physical assets in industrial environments. Here's how SLI works, step-by-step:
- Analyzes the collected data using machine learning algorithms to detect potential threats.
- Identifies patterns and anomalies that may indicate a security breach.
- Analyzes the collected data using machine learning algorithms to detect potential threats.
- Identifies patterns and anomalies that may indicate a security breach.
- Provides real-time monitoring of the system to ensure quick detection of any security incidents.
- Alerts security personnel to take immediate action when a threat is detected.

- Automates responses to common security incidents to minimize the impact and ensure quick resolution.
- Implements pre-defined security policies to handle detected threats effectively.
- Data restoration and system reboot procedures are in place.
- Regular audits and compliance checks are performed.
Advanced Threat Detection
- Utilizes sophisticated algorithms and machine learning to identify potential security threats in real-time.
- Monitors network traffic, system logs, and other data sources to detect anomalies and malicious activities.

Robust Access Control
- Implements strict access control measures to ensure that only authorized personnel can access critical systems and data.
- Uses multi-factor authentication, role-based access control, and encryption to safeguard sensitive information.
Data Integrity and Protection
- Ensures that data remains accurate and unaltered during transmission and storage.
- Uses cryptographic techniques to protect data from unauthorized access and tampering.

Incident Response and Recovery
- Prepares for potential security incidents by having a robust incident response plan in place.
- Ensures quick recovery from security breaches with minimal impact on operations.

Compliance and Auditing
- Adheres to industry standards and regulations to ensure compliance with legal and regulatory requirements.
- Regularly audits systems and processes to identify and address vulnerabilities.

Contact Us
We would love to hear from you! Whether you have questions, need support, or want to learn more about our solutions, feel free to reach out.
© 2024 All Rights Reserved.